Kubernetes
Our engineers implement Kubernetes for data protection-focused private clouds with Swiss and European hosting providers or onto AWS, Azure, and GCP hybrid or public cloud. Our work spans the full scope – from Kubernetes architecture, cluster deployment, configuration, security, IAM, integration, ongoing production and support, etc. Terraform, CI/CD, GitOps.
About
Kubernetes cluster deployment
We help our customers define the target architecture of the application stack to containerize. Application modernization and migration to Kubernetes are part of our core offering. In terms of Kubernetes infrastructure, we offer the full range: from deployment and configuration of clusters on premise or with premium Swiss Kubernetes hosting providers to the managed Kubernetes services of Azure, AWS or GCP.
We monitor, evaluate and eliminate security vulnerabilities of new or existing Kubernetes clusters. Kubernetes IAM, API, RBAC, and network identity.
Cluster Deployment and Configuration
Application Migration to Kubernetes
Cluster Security and IAM
Cluster Production and Support
How
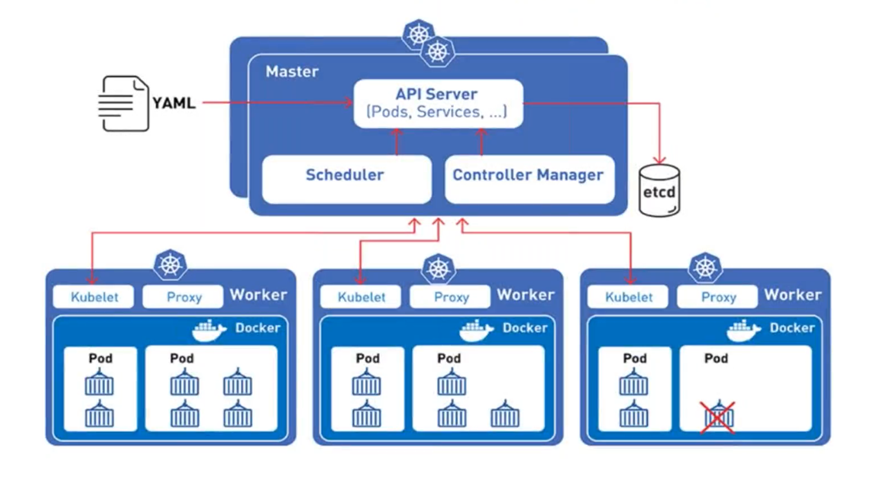
Migration to Kubernetes
Before applications can migrate to containers, the application code needs to be built into a container image. We then proceed in the following order: 1/ building containers for standard dependencies, 2. building containers for the core components, which can be one or several, 3/ preparing a k8s cluster for the POC platform, 4/ creating the deployment Helm charts, and 5/ deploying and debugging until the POC application works flawlessly. We will then ensure a testing and feedback session with defined business and technical stakeholders. After which, we will proceed to the full application containerization and migration to Kubernetes.
How
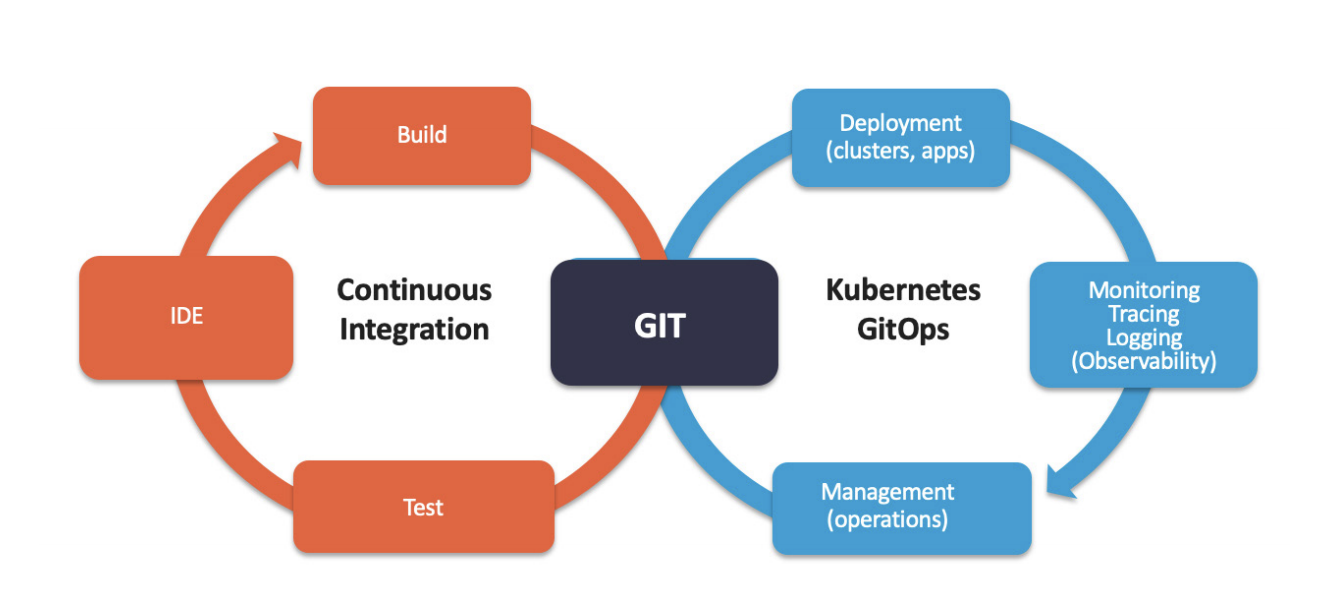
CI/CD, GitOps, IaC
Most of the legacy applications we have modernized are based on a classic three-tier monolithic architecture. The optimal approach we would agree on with customers has most often been a migration to a service-oriented architecture. In this approach we follow a two-step process. In the first step, we will analyse the application to identify the dependencies, frameworks, databases, caching, subsystems, APIs, and IAM architecture. Still in this step, we will identify the necessary open source containerization technologies, and identify the “must-do”, minimally required refactoring of some components. As a second step, we will propose and agree on the SOA target architecture of the future containerized application. This architecture will comprise the optimal number of application components to transform to containers – examples can be the IDP / SSO, Caching, database, LDAP, etc. The resulting architecture will be the shortest and most cost-effective path to legacy monolith.